
The revolution introduced by the digitization process has made it possible to generate and collect increasingly expanding volumes of data. As a result, public and private organizations must define new strategies, design and implement protection systems, adapt their operational models, and learn to manage information by mitigating the risks linked to cyber threats — while remaining in compliance with the provisions of the main regulations in force. In this Viewpoint, we describe the measures organizations must take to mitigate risks.
MORE DATA, MORE ATTACKS!
Data is a fundamental business asset. Its loss or compromise can significantly harm companies and organizations in terms of financial performance, brand reputation, or loss of customers. Whether an organization leverages data to run its business, or data is a byproduct of conducting day-to-day operations, or the institution sells data assets as a one-off product, all data must be managed, protected, tracked, and updated. The economic value of data is further amplified as enterprises go through digital transformation, leading to increased data production.
Organizations have not yet grasped all aspects concerning data, including these important considerations:
-
Who can access the data, and what data can they see?
-
How can data be protected from illicit access attempts?
-
How competent are users, and how do you ensure they continue to be informed about risks associated with processing of information?
In the Viewpoint “The Cyber Battlefield,” Arthur D. Little (ADL) shared several strategies for companies to establish cybersecurity capabilities. While most data security breaches (74%, according to Verizon) are generated by internal user error, employing IT systems such as privileged access management allows organizations to govern user access to information, limiting the risk of unauthorized access. At the same time, it is possible to adopt solutions (e.g., security information and event management) to control who accesses what and monitor how data is changed. Such IT systems enable organizations to detect abnormal behaviors that can be traced back to malicious access attempts, allowing timely intervention. Investments like these enable organizations to respond proactively to the risks generated by cyberattacks.
Nevertheless, as data increases exponentially, there has been a continuous growth of cyberattacks (although a direct correlation has not been proven). Infosecurity Magazine reports that cyberattacks against government agencies and public sector services increased by an astounding 40% in the second quarter of 2023 over the first quarter. BlackBerry Cybersecurity claims it stopped 1.5 million attacks over the 90 days from March to May 2023, of which 55,000 targeted the public sector. Analysis of data shows that cyberattacks have intensified since end of the first quarter of 2023. According to BlackBerry, the highest distribution of cyberattacks during that period included:
-
Financial institutions
-
Healthcare services and equipment
-
Government/public entities
-
Critical infrastructure
Further analysis of the types of attack reveals the reasons behind a cyberattack fall into two categories:
-
Economic. Perpetrated by criminal organizations, these attacks take advantage of a variety of available tools (e.g., ransomware, distributed denial-of-service [DDoS], malware, phishing) to return a profit. As an example, consider the case of the UK’s Royal Mail, which, following a ransomware attack in January 2023, refused to pay the £67 million (about US $85 million) the perpetrators demanded.
-
Political. These attacks are, at their base, related to political issues (sometimes local but more often international). They can often be traced to acts of activism but may also be used to foment cyber wars and can be compared to acts of terrorism. For example, in November 2023, Russian hackers breached 22 Danish power companies in the context of tensions between the Russian Federation and the NATO blockade.
Considering the high costs of data breaches in terms of money (IBM estimates the average cost of a data breach in 2023 to be US $4.45 million), time, and reputation, the importance of preventing attacks is abundantly clear. For this reason, organizations must:
-
Understand the regulatory landscape — to unlock the value of data; protect data from unauthorized access, disclosure, alteration, or destruction; and maintain the privacy of individuals and organizations
-
Commit to increasing investments in defensive technological solutions — with the goal of better understanding competition, customers, and technological trends; supporting business growth; and ensuring secure management of information
-
Adopt standards and frameworks and define business practices — to guarantee a qualitative and quantitative level of information security, continuously adapting to the growing number of attacks and balancing data sharing with protection (see the ADL Viewpoint “Harnessing External Data Sharing to Unlock Transformative Collaboration”).
REGULATORY LANDSCAPE TRANSFORMATION
According to DemandSage, an average of 328.77 million terabytes of data is created every day. But the ability to ensure the proper management and protection of data remains elusive. While from a security and privacy perspective the EU General Data Protection Regulations (GDPR) has raised a shield to defend information, the regulation of big data use still awaits final approval of the EU Data Act, which is joined by the AI Act (legislation focused on regulating data analysis processes based on artificial intelligence [AI] technology). Both legislative acts face a path of about 12 months (end of 2024) awaiting definitive approval by the EU. Thereafter will begin the process in which the acts are transposed into national law by EU countries.
Although GDPR’s reach extends only to personal data, the Data Act encompasses both personal and nonpersonal data, making its range of application notably wider. The Data Act aims to eliminate data-access hurdles for both public and private organizations, making it simpler to transfer data among service providers and encouraging a broader range of participants, including small and medium-sized enterprises, to engage in the data economy. These new regulations will empower consumers and businesses to have a voice in determining the usage of data produced by their connected devices.
Additionally, with increasing integration of AI systems into everyday life, issues surrounding data protection and ethical considerations have come to the forefront. Cybercriminals could use AI to easily develop malware that can discover previously unknown vulnerabilities or evade detection and create sophisticated phishing attacks. GDPR supports the creation of AI and big data applications that effectively strike a balance between data protection and other societal and economic interests yet offers limited guidance on accomplishing this objective. Consequently, the AI Act aims to regulate AI through a risk-based approach, which differentiates compliance obligations based on the potential risk that intelligent software and applications may pose to fundamental rights. The higher the risk, the more substantial the compliance requirements and responsibilities for the creators of smart applications.
The completion of the regulatory path for both the Data and AI Acts by EU countries will require public and private organizations to adapt within certain time frames and change processes, committing new budgets and adapting business models to ensure compliance.
COMMITMENT TO INVESTMENTS
The growth in data availability is leading companies, both public and private, to make ever greater investments in the acquisition of tools and technologies for their management. The aim is to know about the competition, customers, and innovative technological trends and tools; to support business growth through the planning and implementation of effective strategies; and to ensure the secure management of information.
But while investments have focused on the acquisition of know-how for the analysis, processing, and visualization of information and technological tools like business intelligence, data analytics, and AI systems, a report published by the European Union Agency for Cybersecurity (ENISA) highlights numbers linked to the main growth drivers of information security spending in 2023. The report identifies the main drivers of the increase as hybrid working, transition from virtual private networks (VPNs) to zero-trust network access, and the move to cloud-based deployment models. The study estimates an overall growth in spending in 2023 of $143 billion, and the estimate for 2024 stands at $163 billion, with a growth of up to 14% (see Figure 1).
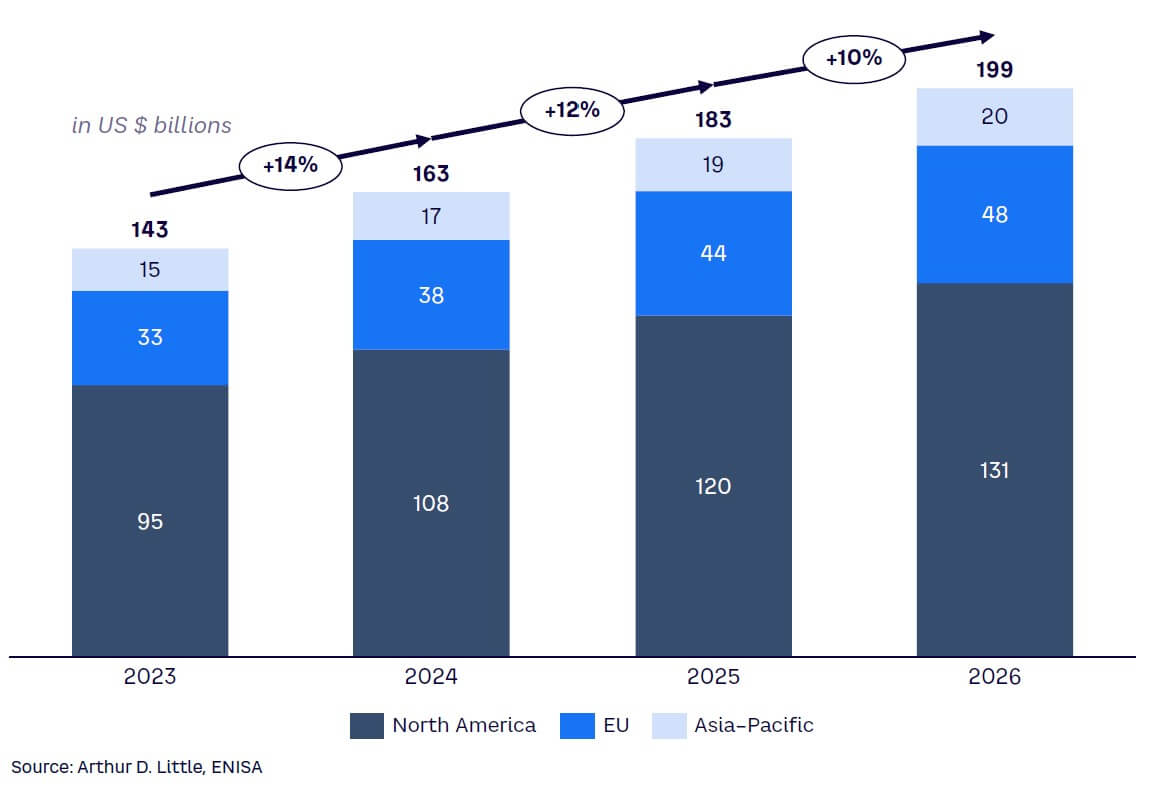
The report predicts sustainable growth through 2026, with double-digit percentages every year. By geographical area, North America represents, on average, two-thirds of annual global spending. The gap between North America and other areas highlights a greater focus on security issues in this region and emphasizes the need for other areas to increase investments to bridge the technological and cultural gap.
According to the ENISA report, the largest increases in spending in 2024 concern cloud security (+24% year-over-year [YoY]), in accordance with the substantial and general migration process from proprietary on-premises architectures to cloud solutions, and data privacy (+24% YoY), as the organizational focus remains the processing of data for privacy purposes (see Figure 2).
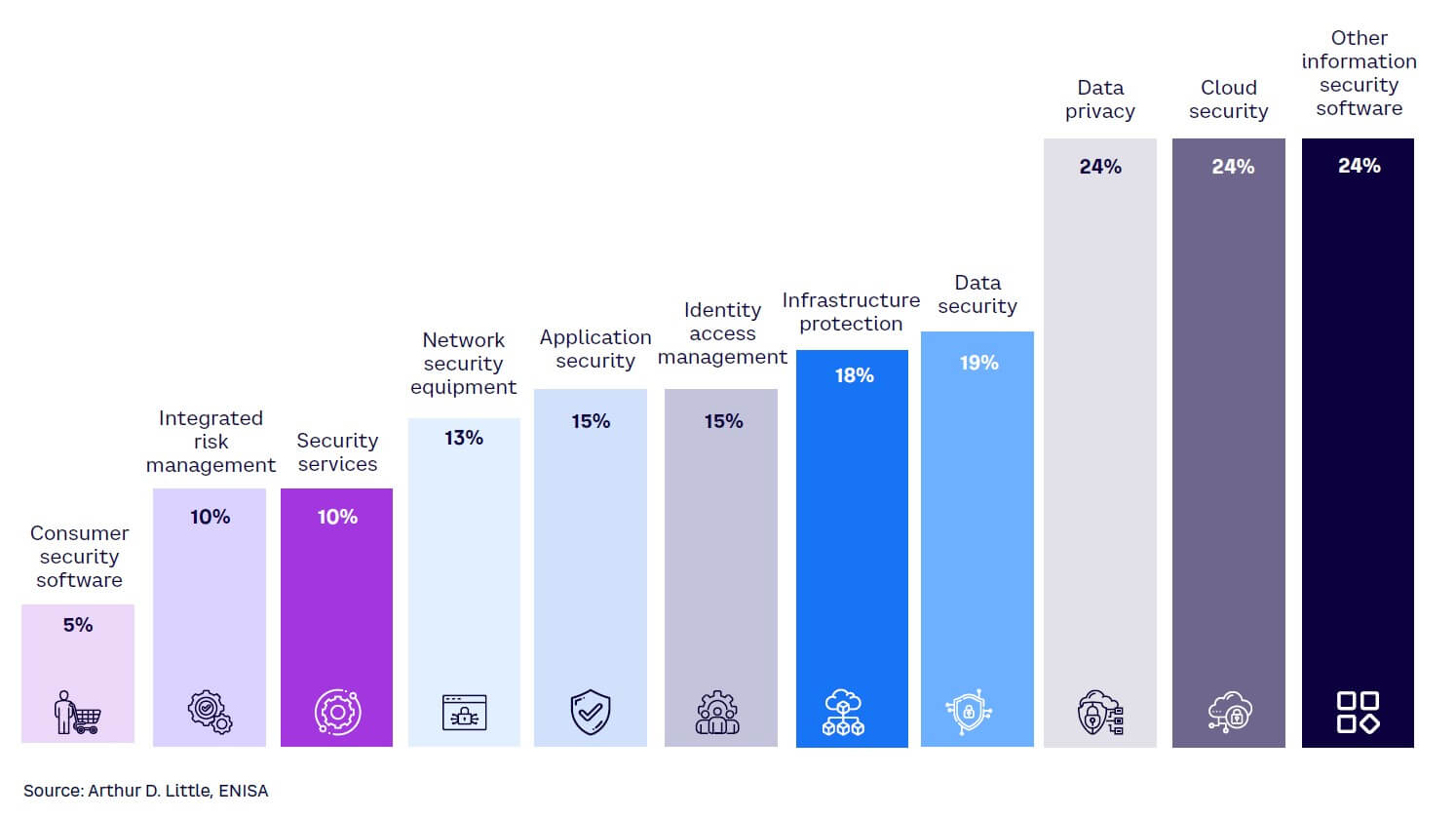
The factors behind these numbers are linked to the growing risk of cyber threats as well as the changes affecting organizations and their operating models in the process of adapting to the new business paradigm, which acknowledges data as a fundamental asset for companies, both public and private. This value makes the level of security implemented and perceived increasingly critical: first, to guarantee regulatory compliance and secure the value that the company will be able to generate from access to information, and second, as an element that is of concern to stakeholders and shareholders.
APPLYING PROPER FRAMEWORKS & BUSINESS PRACTICES
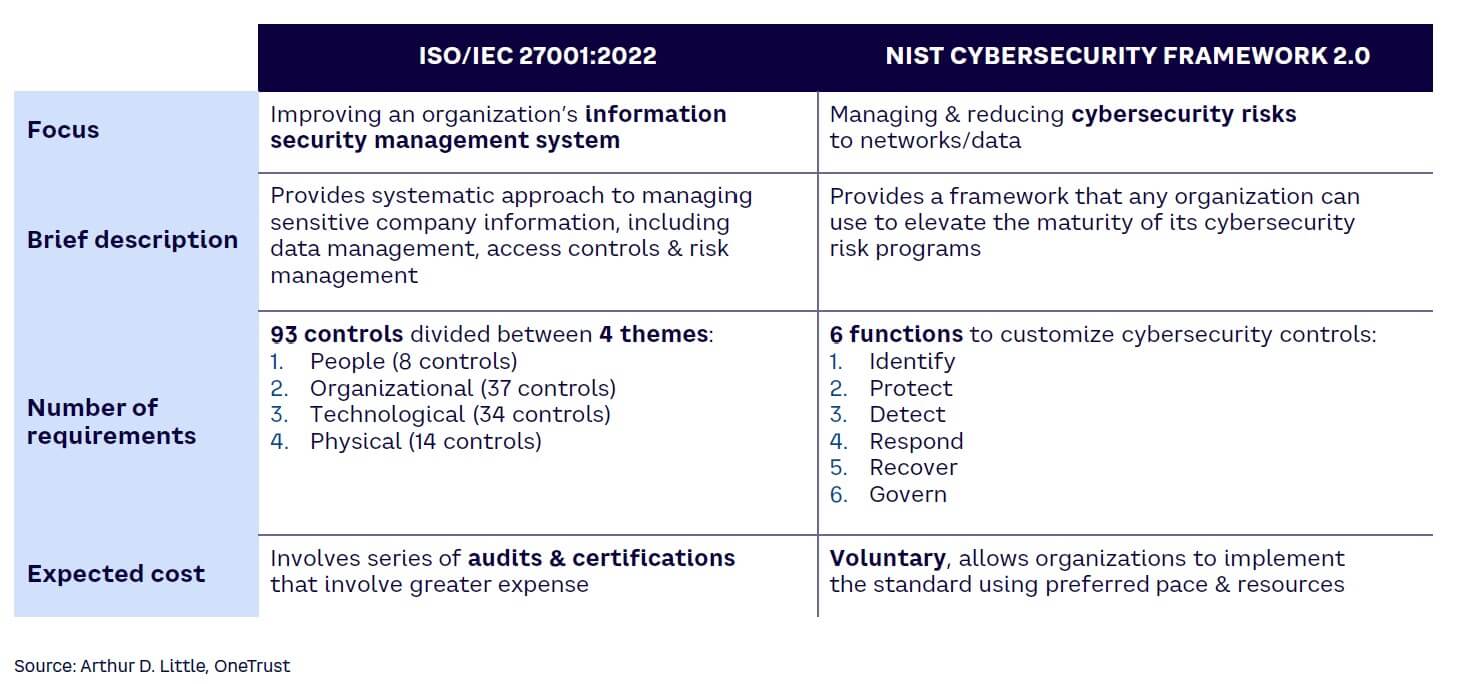
A structured framework is crucial for effective information security management. In considering information security and personally identifiable information (PII) protection, organizations can refer to widely recognized standards such as ISO/IEC 27001:2022 or the NIST Cybersecurity Framework (CSF). These standards offer structured frameworks and best practices for evaluating and mitigating information security risks. The adoption of an organizational framework can enhance time to market by standardizing processes, automating security and privacy compliance, and establishing consistent measures.
Table 1 highlights the main characteristics of the two frameworks, but it is important to specify that these frameworks often cover the same areas, such as identifying risks, implementing controls to reduce risks, and monitoring performance. An organization can integrate the frameworks synergistically to create a holistic approach to cybersecurity.
Adopting a standard framework allows organizations to achieve a series of benefits, including:
-
Information security awareness — enabling the implementation of robust measures for safeguarding sensitive information
-
Risk mitigation — gaining a deeper understanding of risk management and providing the ability to identify vulnerabilities, assess risks, and implement strategies to mitigate them
-
Regulatory compliance — complying with relevant laws and evolving regulations, providing a proactive approach to maintaining information security
-
Enhanced reputation — increasing an organization’s reputation and providing greater confidence of an organization’s customers and partners, fostering better relationships and creating additional business opportunities
-
Cost savings — following the initial investment, prompting medium/long-term benefits due to increasing information security “culture,” decreased likelihood of breaches, and subsequent reduction in legal fees and reputational damage
In general, the ISO/IEC 27001:2022 standard is useful for operationally mature organizations that aim to put in place or improve their entire information security management cycle and are seeking certification to demonstrate the company’s dedication to security and compliance. Conversely, the NIST CSF is more suited to evaluating maturity in the first stages of developing a cybersecurity risk management plan or in attempts to mitigate prior failures or data breaches.
By aligning with these well-established standards, organizations can methodically identify and address potential threats, safeguarding both information security and privacy, while demonstrating their commitment to compliance and data protection. It is important to remember that there is no one-size-fits-all approach, so every organization must choose the model that best suits its needs.

Conclusion
SECURITY CONTINUOUS IMPROVEMENT
Increases in data and digitalization processes have led to an escalation of cyberattacks against companies and institutions as well as to a continuously evolving regulatory environment and a need for companies to constantly adapt to the changing dynamics of the data economy. Thus, organizations must invest in technologies for prevention and protection, while at the same time provide communications and trainings to ensure their people are aware of the culture of security as good business practice. Overall, organizations must manage the evolution of regulations and technology transformation, paying particular attention to:
-
Assessing information security maturity and the level of risk exposure
-
Identifying and adopting frameworks to adapt to international standards and regulatory compliance requirements
-
Defining an adequate budget and embracing technology improvements to proactively respond to the risks of cyberattacks


